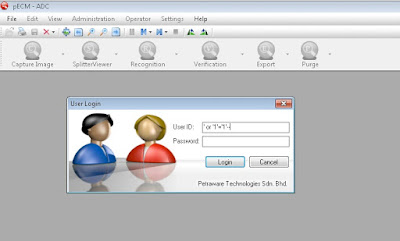
My 1st ever CVE ID
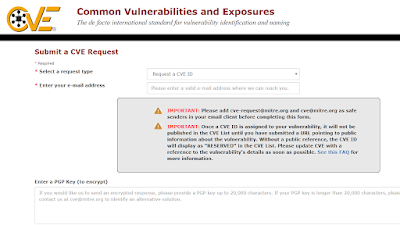
Hi guys, I am really excited for my 1st ever CVE ID. So today, I will share the breakdown of the process for getting the CVE ID. Maybe there are other blogs or websites sharing this process, but I wanted to share my journey on getting it. I'm relatively new in this field so pardon for my little knowledge that I have. I'm doing this for my own experience and knowledge. Also for the love of anything related to security. Below are the steps I've taken for the process. 1) Find vulnerability on your target. You can check whether your target is on the list of participating CNA . If it is not under any CNA , you can request it at MITRE Corporation . You can check the list of participating CNA here: https://cve.mitre.org/cve/request_id.html 2) After that, you can request it via web form here: https://cveform.mitre.org/ The process is quite simple. You simply fill in the form with required information and in 24 hours, they will respond to your email. 3) You wi